US intelligence agencies are tasked with investigating the recent ransomware and supply chain attacks. Will white hats lead the way, or has a fox just been set loose to guard the hen house?
WikiLeaks’ Vault 7 provides documentation on CIA hacking capabilities that can fake the origins of a cyberattack, leading investigators to blame the wrong country, such as Russia.
“Marble is used to hamper forensic investigators and anti-virus companies from attributing viruses, trojans and hacking attacks to the CIA” — WikiLeaks Vault 7, 2017
As such, the CIA is capable of hiding the true origins of a cyberattack while making it seem like the attack came from a country that speaks Russian, Chinese, Arabic, Korean, or Farsi.
We know this thanks to WikiLeaks’ “Vault 7” documents on the CIA’s hacking abilities.
With regards to the recent rise in major ransomware attacks, could malware and other cyber tools developed by the CIA still be making their rounds?
CIA ‘Marble’ tool capable of faking cyberattack origins appearing to come from Russia, China, or Iran
Among the many CIA hacking capabilities published by WikiLeaks in March, 2017, Vault 7 describes a CIA tool known as the “Marble” framework.
According to WikiLeaks:
“Marble is used to hamper forensic investigators and anti-virus companies from attributing viruses, trojans and hacking attacks to the CIA.
“Marble does this by hiding (“obfuscating”) text fragments used in CIA malware from visual inspection.
“This is the digital equivalent of a specialized CIA tool to place covers over the English language text on US-produced weapons systems before giving them to insurgents secretly backed by the CIA.”
Within the Marble framework lies code that can confuse the true origins of a cyberattack — leading forensic investigators to the wrong conclusions.
According to WikiLeaks:
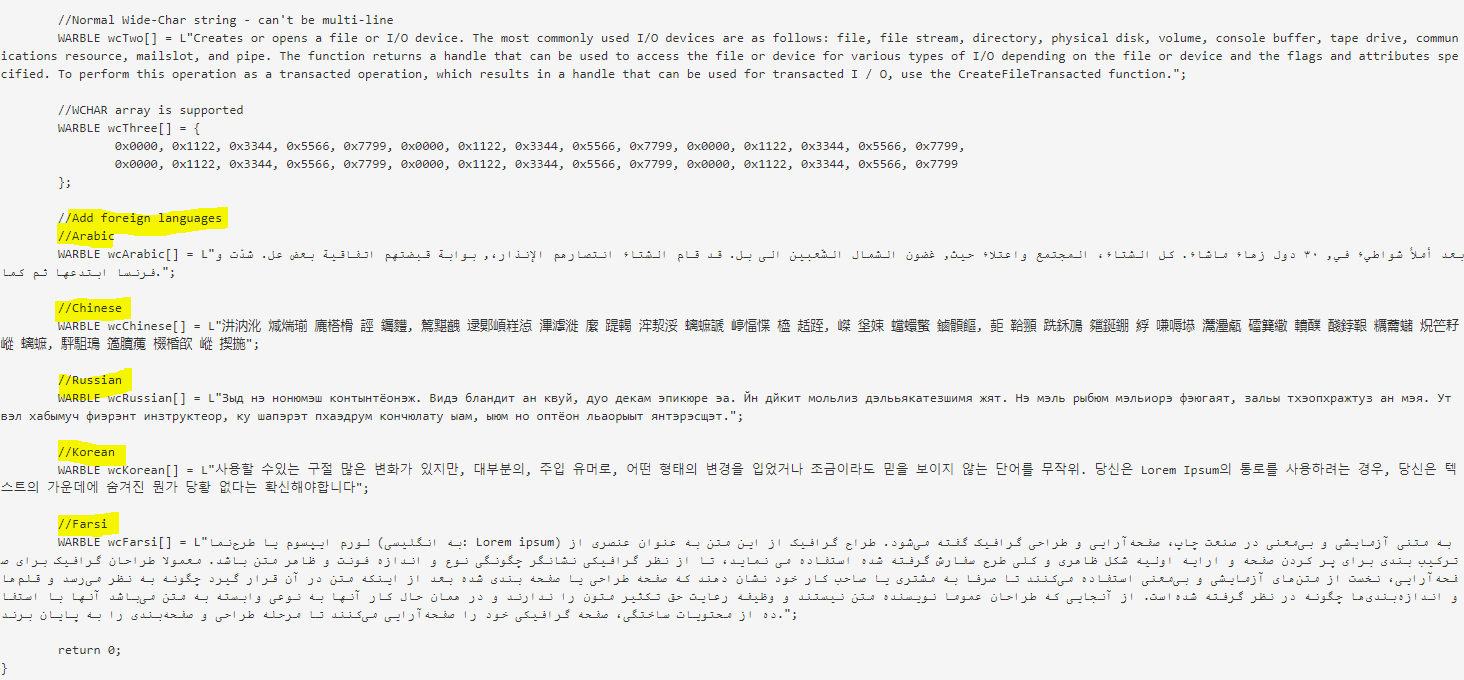
“The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi.
“This would permit a forensic attribution double game, for example by pretending that the spoken language of the malware creator was not American English, but Chinese, but then showing attempts to conceal the use of Chinese, drawing forensic investigators even more strongly to the wrong conclusion, — but there are other possibilities, such as hiding fake error messages.”
This year, major cybersecurity firms are reporting that CIA malware is still in circulation, and they can confirm this by referencing WikiLeaks’ Vault 7.
CIA malware is still in circulation, industry calls it ‘Lambert’ or ‘Longhorn’ malware
Malware resembling those found in Vault 7’s CIA hacking tools cache go by the industry names of “Lambert” by Kaspersky and “Longhorn” by Symantec.
In April, 2021, Kaspersky reported that in 2019, “multiple antivirus companies received a collection of malware samples,” and that some of “the samples have intersections of coding patterns, style and techniques that have been seen in various Lambert families“.
“There can be little doubt that Longhorn’s activities and the Vault 7 documents are the work of the same group” — Symantec, 2017
Again, Lambert = CIA = Longhorn.
In another report, Symantec directly cites WikiLeaks’ Vault 7 to claim that Longhorn [Lambert] malware comes from the same group:
“The tools used by Longhorn closely follow development timelines and technical specifications laid out in documents disclosed by WikiLeaks.
“The Longhorn group shares some of the same cryptographic protocols specified in the Vault 7 documents, in addition to following leaked guidelines on tactics to avoid detection.
“Given the close similarities between the tools and techniques, there can be little doubt that Longhorn’s activities and the Vault 7 documents are the work of the same group.”
Whether its called Lambert or Longhorn, malware developed by the CIA is still being found in circulation.
WikiLeaks showed us that the CIA was responsible for developing the Marble framework and many other hacking capabilities, but who is to say that these tools stayed in the hands of the CIA?
Could some other group(s) have access to CIA malware and frameworks?
Intelligence Community to investigate ransomware, supply chain cyber attacks
The intelligence community and corporate media are quick to attribute recent ransomware attacks to hackers in Russia, yet the intelligence community has a history of furthering its own hidden agendas, and the corporate media often employs former members of the intelligence community as expert commentators.
On Saturday, US President Joe Biden ordered the intelligence community to investigate who was behind the most recent attack on Kaseya that affected between 1,500 and 2,000 businesses.
One business in particular, Sweden’s Coop supermarket chain, had to close around 500 of its stores due to the cyberattack.
In addition to the Kaseya attack, this year we have seen major ransomware attacks on Colonial Pipeline, Ireland’s Health Service Executive, and JBS foods — just to name a few.
In each case, the cyberattacks were attributed to criminal gangs operating out of Russia, and while there is ample evidence for the validity of these claims, the fact remains that America’s own intelligence community has long since developed the necessary tools to hide the true origins of cyberattacks.
“In February 2019, multiple antivirus companies received a collection of malware samples […] Some samples have intersections of coding patterns, style and techniques that have been seen in various Lambert families” — Kaspersky, 2021
This year’s supply chain and ransomware attacks have largely been attributed to two groups — REvil and DarkSide — which, according to “experts,” appear to originate in Russia.
We could leave it at that and believe that the ransomware attacks come from Russian gangs looking to make a profit because the business model is so lucrative.
But from another perspective, could the cyberattacks and subsequent ransomware payoffs, be a means to finance covert intelligence operations?
If by some chance the intelligence community, along with five-eyes partners were ever to be involved in such a scheme, what purpose could it possibly serve?
It’s an interesting rabbit hole to go down, but who knows if it would turn up anything?
An anticipated cyber pandemic heats up
While the origins of cyberattacks are important for cybersecurity teams, the fact remains that major cyberattacks are on the rise, and globalists are telling us that a coming cyber pandemic will be even worse than the coronavirus crisis.
“We all know, but still pay insufficient attention to, the frightening scenario of a comprehensive cyber attack, which would bring a complete halt to the power supply, transportation, hospital services, our society as a whole” — Klaus Schwab, WEF, 2020
Prior to the major ransomware attacks on critical infrastructures this year, the World Economic Forum (WEF) released a short video on January 18, 2021 warning about a “cyber attack with COVID-like characteristics” that would “spread faster and further than any biological virus.”
“The only way to stop the exponential propagation of a COVID-like cyber attack threat,” according to the WEF, “is to fully disconnect the millions of vulnerable devices from one another and from the internet.”
But, “A single day without the internet would cost our economies more than $50 billion, and that’s before considering economic and societal damages should these devices be linked to essential services, such as transports or healthcare.”
Prepping for a cyber pandemic continues.
On July 9, 2021 the World Economic Forum and partners will host their annual Cyber Polygon exercise.
Cyber Polygon 2021 will hold live training exercises responding to “a targeted supply chain attack on a corporate ecosystem in real time.”
“The COVID-19 crisis would be seen in this respect as a small disturbance in comparison to a major cyber attack” — Klaus Schwab, WEF, 2020
Running parallel to the training exercise will be discussions on how to tackle everything from ransomware and supply chain attacks to implementing “resilient” digital currencies, and a desire for global governance on the internet.
In his opening remarks at Cyber Polygon 2020, World Economic Forum (WEF) Founder and Executive Chairman Klaus Schwab warned about a coming “cyber pandemic” that would be worse than the current global crisis.
“We all know, but still pay insufficient attention to, the frightening scenario of a comprehensive cyber attack, which would bring a complete halt to the power supply, transportation, hospital services, our society as a whole,” he said.
“The COVID-19 crisis would be seen in this respect as a small disturbance in comparison to a major cyber attack.”
Event 201 and Cyber Polygon: A glimpse of what may come?
The WEF and partners have been remarkably prophetic in simulating a crisis just before it happens.
Just a few months before the COVID-19 coronavirus outbreak, the WEF, along with the Johns Hopkins and the Bill and Melinda Gates Foundation, held a fake pandemic exercise on October 18, 2019 called Event 201, which specifically simulated a coronavirus pandemic to gauge global preparedness.
Event 201 simulated “an outbreak of a novel zoonotic coronavirus transmitted from bats to pigs to people that eventually becomes efficiently transmissible from person to person, leading to a severe pandemic,” according to the Event 201 scenario page.
“The pathogen and the disease it causes are modeled largely on SARS, but it is more transmissible in the community setting by people with mild symptoms.”
“It is important to use the COVID-19 crisis as a timely opportunity to reflect on the lessons of cybersecurity community to draw and improve our unpreparedness for a potential cyber pandemic” — Klaus Schwab, 2020
The Event 201 recommendations called for greater collaboration between the public and private sectors while emphasizing the importance of establishing partnerships with unelected, global institutions such as the WHO, the World Bank, the International Monetary Fund, and the International Air Transport Organization, to carry out a centralized response.
Who benefits the most from government lockdowns and the most recent cyberattacks that have crippled the economy?
Given the unelected globalists’ remarkably accurate track record on simulating events shortly before they happen, is the WEF anticipation of a cyber pandemic already upon us, or is the worst still yet to come?
Intelligence Community: White hat or a fox opening the hen house for a great reset?
When WEF Founder Klaus Schwab officially launched his agenda for a great reset of the global economy and societal contracts in June, 2020, he declared, “The world must act jointly and swiftly to revamp all aspects of our societies and economies, from education to social contracts and working conditions.”
If the goal is to reset the economy and all societal contracts, could the recent cyberattacks on critical infrastructures somehow further that agenda?
“The world must act jointly and swiftly to revamp all aspects of our societies and economies, from education to social contracts and working conditions” — Klaus Schwab, WEF, 2020
For more than a year, the World Economic Forum and partners have been prepping for a potential cyber pandemic.
Like clockwork, the world has been rocked by a wave of cyberattacks on critical infrastructure since the conclusion of Cyber Polygon 2020.
Now, the US intelligence community has been tapped for investigating the origins of recent ransomware attacks, and why not?
Who would know better about finding the hidden origins of a cyberattack than the intelligence community? They developed many of the tools and tactics, after all.
But will the US intelligence community accurately get to the bottom of these attacks and release their findings with honesty, openness, and transparency, or has a fox just been set loose in the hen house to help make room for the great reset?
Prepping for a cyber pandemic: Cyber Polygon 2021 to stage supply chain attack simulation
US considers going after ransomware attackers like it used to hunt pirates at sea: Senate hearing
‘Ransomware is quickly becoming a national emergency’ amid pandemic: CISA acting director testifies