The Pentagon’s Irregular Warfare Technical Support Directorate (IWTSD) is developing tools for PSYOP missions and information warfare, including social media mapping, behavioral manipulation, surveillance, and targeted influence campaigns.
The IWTSD is the Pentagon’s lesser-known research and development branch that delivers some of the most powerful psychological operations (PSYOP) tools and other irregular warfare capabilities to defense and intelligence entities.
Toolkits for information warfare, social network mapping, behavioral manipulation, surveillance, and targeted influence campaigns are funded, organized, and delivered through the IWTSD.
These tools for irregular warfare are developed by “businesses of all sizes and types, educational institutions, government agencies, and nontraditional submitters,” including international partners from Australia, Canada, Israel, Singapore, and the UK.
“PSYOP Forces are Masters of Influence – the core of information warfare. We conduct influence activities to target psychological vulnerabilities and create or intensify fissures, confusion, and doubt in adversary organizations” — US Army Special Operations Command
While similar to DARPA in some ways, the IWTSD is not just about funding research and development for irregular warfare, but also operationalizing those capabilities as quickly and effectively as possible while transitioning technologies to the appropriate agencies.
Born out of the Combating Terrorism Technical Support Office, the IWTSD’s stated mission is “to identify and develop capabilities for DoD to conduct Irregular Warfare against all adversaries, including Great Power competitors and non-state actors, and to deliver those capabilities to DoD components and interagency partners through rapid research and development, advanced studies and technical innovation, and provision of support to US military operations.”
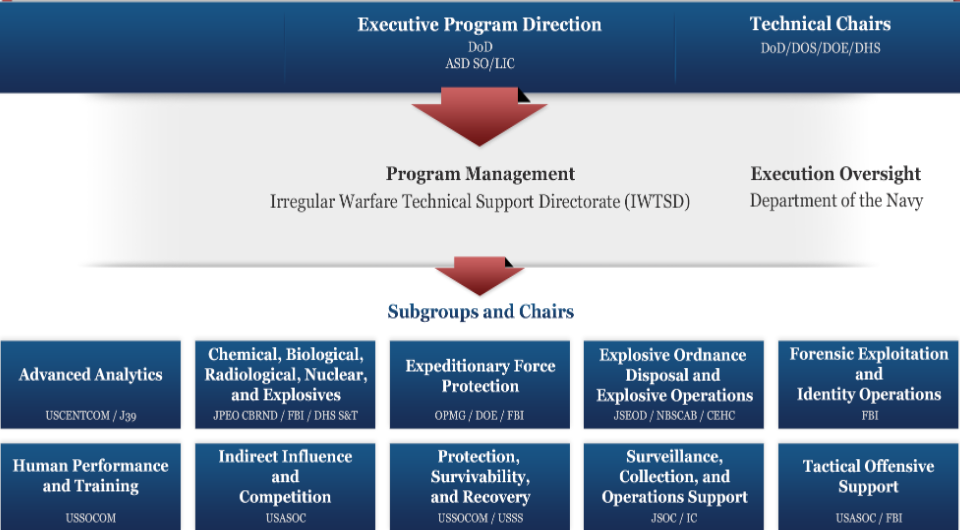
Here, we take a look at some of the unclassified research programs dealing with mass surveillance and psychological influence operations that the IWTSD is funding to further its mission.
The following IWTSD broad agency announcement excerpts for FY2023 are taken from a downloadable document published on March 23, 2022, and all initial submissions were due on April 22, 2022.
PSYOP: Information Warfare Enabler Kit — Detachment
The United States Army Special Operations Command describes PSYOP Forces as “Masters of Influence – the core of information warfare” that “conduct influence activities to target psychological vulnerabilities and create or intensify fissures, confusion, and doubt in adversary organizations.”
They “use all available means of dissemination – from sensitive and high tech, to low-tech, to no-tech, and methods from overt, to clandestine, to deception.”
“The PSYOP Regiment has been testing and refining the concept of a commercial-off-the-shelf based integrated solution for the Psychological Operations Detachment” — Information Warfare Enabler’s Kit — Detachment, Irregular Warfare Technical Support Directorate
Under the category of Indirect Influence and Competition, the IWTSD is further developing its Information Warfare Enabler Kit — Detachment (IWEK-D), which is “a commercial-off-the-shelf (COTS) based integrated solution for the Psychological Operations Detachment (PSYDET).”
According to the announcement, “Most equipment that is assigned to PSYOP units has been designed to be utilized in an overt tactical environment, not a regional/global one.
“This has created a distinct gap in which all gear looks highly conspicuous in non-conflict environments, dramatically increasing operational security (OPSEC) and force protection (FORCEPRO) concerns with its use.”
Now, the IWTSD is looking to “refine the components of the kit, maximize component interoperability, develop cloud-based solutions for integration with existing planning tools.”
The IWEK-D kit is divided into three distinct tools: Product Development Tool, Subject Matter Expert Tool, and Effects Tool.
The Product Development Tool includes components that:
- Shoot 4K Video
- Shoot in night vision/low light conditions
- Have the ability to run mobile podcasts, audio interviews, and other similar capabilities
- Provide lighting solutions for visual product development
- Provide digital sound mixing solutions
- Provide solar based power solutions for austere environment operations
- Edit and store up-to 4 TB of digital material and content
“Include the ability for the user to craft and monitor Internet of Things (IOT) devices created from open source components such as raspberry pis, Arduino boards, and USB GPS receivers” — Information Warfare Enabler’s Kit — Detachment, Irregular Warfare Technical Support Directorate
The Subject Matter Expert Tool includes components that:
- Have at least 8 hours of operational battery life on a single charge
- Project 4K quality video in an indoor environment and 1080p in an outdoor environment
- Provide solar based power solutions for austere environment operations
- Provide a small form factor camera that is waterproof
- Provide Data blocking options for all USB components
- Shall match a business professional aesthetic
- Shall provide alternative bags for rural or austere employment
The Effects Tool includes components that:
- Passively monitor the surrounding Radio Frequency (RF) Environment
- Run multiple Virtualized Machines (VMs) with optimization for open source VM solutions such as VM-Ware, or Virtual Box
- Include the ability for the user to craft and monitor Internet of Things (IOT) devices created from open source components such as raspberry pis, Arduino boards, and USB GPS receivers
- Shall be able to transmit data packets on the Wi-Fi, Bluetooth, and ZigBee ranges
- Contain small form factor RF detection capabilities
- Shall have the ability to integrate open source IR cameras with small form factor boards
- Shall match either an “E-Sports”/gamer aesthetic or an IT professional’s profile
So, the idea is to create a physical kit for PSYOP units that doesn’t look conspicuous, can blend in with its surrounding, and is capable of spying on its environment and relaying information while hiding its origin.
Real Social Network Mapping
According to a Newsweek exclusive report from May 17, 2021, the US has a “clandestine army” consisting of “cutting-edge cyber fighters and intelligence collectors who assume false personas online, employing ‘nonattribution’ and ‘misattribution’ techniques to hide the who and the where of their online presence while they search for high-value targets and collect what is called ‘publicly accessible information’—or even engage in campaigns to influence and manipulate social media.”
The Newsweek exclusive highlights the nature of irregular warfare and gives a small glimpse into what some of it looks like in practice.
Now, the Irregular Warfare Technical Support Directorate is looking to develop, test, and evaluate a cloud-based Social Network Mapping software that automates search, extraction, organization, visualization, and mapping functions in order to extract key insights into real-world social networks from PAI [publicly available information] and open-source data.
“The platform must enable users to identify key individuals, groups, topics, and hot spots of activity; identify communities, subgroups, and interest patterns; and examine group membership changes” — Real Social Network Mapping, Irregular Warfare Technical Support Directorate
The Real Social Network Mapping platform will be able to “identify key individuals, groups, topics, and hot spots of activity; identify communities, subgroups, and interest patterns; and examine group membership changes.”
The platform will also enable users to develop individual and network profiles, such as social, political, and business networks.
In the end, it seems that the Real Social Network Mapping platform will make it easier to know everything about an individual or a group, who they associate with, where they are located, and what they are planning on doing, based on automated social networking data collection and analysis.
Enabling Indirect Influence and Competition
On the subject of enabling indirect influence and competition, the Irregular Warfare Technical Support Directorate seeks proposals for the research and demonstration of technically and operationally viable capabilities, methodologies and approaches to more effectively compete and achieve influence advantage across the informational, physical and cognitive arenas.
Proposals shall include solutions that:
- Develop, test and deploy new tools, capabilities and concepts for understanding target motivation, morale and behavioral effects in order to deliver precise and rapid influence at scale to relevant populations in the informational and physical domains
- Apply AI/ML technologies to expedite analysis and/or execution of influence, information, or military deception operations
- Proactive measures to undermine Great Power competitors’ mis- and dis-information, deception and other (e.g., financial) coercion activities
- Bolster the proactive mindset shift required to succeed through unified action in Irregular Warfare missions in order to compete more effectively against all adversaries in IW
“The Irregular Warfare Technical Support Directorate (IWTSD) seeks proposals for the research and demonstration of technically and operationally viable capabilities, methodologies and approaches to more effectively compete and achieve influence advantage across the informational, physical and cognitive arenas” — Enabling Indirect Influence and Competition, Irregular Warfare Technical Support Directorate
This particular announcement had “unspecified requirements” that “are for proposing unique innovations that have not yet been identified by IWTSD.”
Situational Information at the Tactical Edge
Another IWTSD broad agency announcement sought to “develop a software tool for sensitive site exploitation (SSE) and other information collection that can function on commonly available Android mobile devices in a structured and standardized digital format enabling effective, automated dissemination and analysis.
“The tool shall be capable of biometric capture of facial images, contactless fingerprints, and voice samples as well as record interviews” — Situational Information at the Tactical Edge, Irregular Warfare Technical Support Directorate
The tool shall be loadable onto the Android device and enable users to capture data and images from sensitive sites and quickly generate standard multimedia reports and digital site sketches annotated with notes and photographs.
The tool shall be capable of biometric capture of facial images, contactless fingerprints, and voice samples as well as record interviews.
Human-Algorithm Fusion for Facial Recognition
The Pentagon’s Irregular Warfare Technical Support Directorate is looking to improve its facial recognition capabilities by designing, developing, and delivering a software tool that fuses analytic algorithms with the human examiner to analyze, adjudicate and report facial image examinations.
The military, law enforcement, Homeland Security, and intelligence communities require a software tool that fuses human and machine learning capabilities to meet or exceed the facial recognition accuracy of forensic facial examiners while reducing the analysis time required for review and consensus between them.
“Collaboration with our performer partners, coupled with millions of RDT&E dollars invested each year, has allowed the IWTSD to provide the DoD, the interagency, and international partners with the advanced technology and capabilities they need to carry out their mission of irregular warfare” — Irregular Warfare Technical Support Directorate
The IWTSD partners with both foreign and domestic performers, including academic institutions, private companies, national and international research labs, and government agencies.
Foreign partners include:
Australia
- Defence Science and Technology Group, Canberra, Australian Capital Territory
- Defence Science and Technology Group, Fisherman’s Bend, Melbourne, Victoria
- Flinders University, Adelaide, South Australia
- Queensland Fire and Rescue Service, Brisbane, Queensland
- Queensland University of Technology, Brisbane, Queensland
- Translational Research Institute Australia, Woolloongabba, Queensland
- University of Adelaide, Adelaide, South Australia
- University of Melbourne, Parkville, Victoria
- XTEC Limited, Adelaide, South Australia
Canada
- AirBoss Defense, Acton Vale, Quebec
- Public Health Agency Canada, Winnipeg
- Public Safety Canada, Ottawa, Ontario
- Royal Canadian Mounted Police, Regina, Saskatchewan
- Uncharted Software, Inc., Toronto, Ontario
Democratic Republic of the Congo
- Institut National de Recherche Biomedicale, Kinshasa
Israel
- CS3 Composite Solutions, Inc., Holon
- Elbit Systems, Ltd., Yokneam
- Genosmart, Modi’in Makabim-Re’Ut Israel Atomic Energy Commission, Tel Aviv
- Israel Defense Forces Israel Ministry of Defense, Tel Aviv
- Israel Security Agency, Tel Aviv
- Pearls of Wisdom Advanced Technologies, Ltd., Kefar Netter
- Prime Minister’s Office Rafael Advanced Defense Systems, Ltd., Haifa
- Tamar Explosives, Ltd., Tel Aviv
Netherlands
- Netherlands Organisation for Applied Scientific Research, The Hague
Singapore
- Defence Science and Technology Agency
- Ministry of Defence
Spain
- SEADM, Valladolid
- SEDET, Valladolid
United Kingdom
- Avon Protection Systems, Inc., Melksham
- BBI Detection, Porton Down
- Cardiff University, Cardiff
- Centre for the Protection of National Infrastructure, London
- Defence Science and Technology Laboratory, Fort Halstead
- Defence Science and Technology Laboratory, Porton Down
- Defence Science and Technology Laboratory, Portsdown West
- Department for Transport, London
- Smiths Detection Watford Limited, Hertfordshire
- University of Bristol, Bristol
By collaborating with its performer partners, coupled with millions of RDT&E dollars invested each year, the IWTSD boasts that it has provided “the DoD, the interagency, and international partners with the advanced technology and capabilities they need to carry out their mission of irregular warfare.”












