The Federal Aviation Administration (FAA) lacks “key practices that are necessary to carry out a risk-based cybersecurity oversight program” with regards to avionics, according to the Government Accountability Office (GAO).
“While FAA recognizes avionics cybersecurity as a potential safety issue for modern commercial airplanes, it has not fully implemented key practices that are necessary to carry out a risk-based cybersecurity oversight program” — GAO report
On Friday, the GAO issued its assessment of the FAA’s cybersecurity efforts and found that while airplane and avionics manufacturers “have undertaken extensive measures” to thwart cyberattacks, the FAA is lacking a comprehensive, risk-based avionics cybersecurity oversight program.
Specifically, the GAO found that the FAA has not:
- Assessed its oversight program to determine the priority of avionics cybersecurity risks
- Developed an avionics cybersecurity training program
- Issued guidance for independent cybersecurity testing
- Included periodic testing as part of its monitoring process
The good news is that “to date, there have been no reports of successful cyberattacks on an airplane’s avionics systems.”
However, without a comprehensive cybersecurity oversight system in place, “the evolving cyber threat landscape, combined with the increasing use of internal networks on airplanes and the increasing connections between airplanes and external sources, could lead to increasing risks for future flight safety.”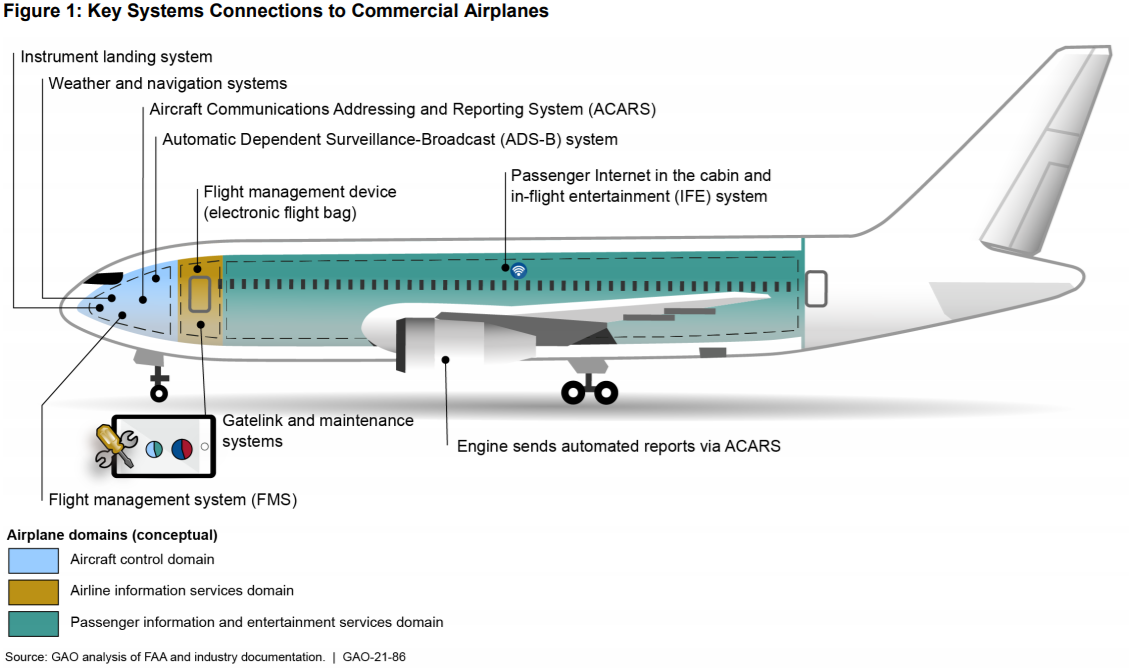 The threats facing the aviation system are numerous and diverse — from outdated legacy systems that are vulnerable to malware to the “growing connectivity between airplane networks and systems and various other systems via the Internet,” and the ever-present risk of insider threats and supply chain insecurity.
The threats facing the aviation system are numerous and diverse — from outdated legacy systems that are vulnerable to malware to the “growing connectivity between airplane networks and systems and various other systems via the Internet,” and the ever-present risk of insider threats and supply chain insecurity.
The 55-page report gives a full list of vulnerabilities to avionics, and here we have highlighted the main bullet points:
- Commercial Software May Not Always Be Updated Promptly to Correct Flaws
- Vulnerabilities Could Be Introduced in the Supply Chain If It Is Not Assessed or Components Are Not Properly Tested
- Systems that Connect to Avionics Could Spread Malicious Software
- Legacy Systems on Airplanes May Lack Up-to-Date Cybersecurity Controls
- Airplane Communications Systems Could be Vulnerable to Flight Data Spoofing
According to the GAO report, bad actors looking to exploit vulnerabilities in flight safety include:
- Cybercriminals — Criminal groups, including organized crime organizations, use cyberattacks for monetary gain
- Nations — Nations, including nation-state, state-sponsored, and state-sanctioned groups or programs, may use cyberattacks as part of
covert activities to gather information about individuals, government organizations, and private sector entities. Nation states may also leverage their espionage and reconnaissance activities to develop capabilities for future computer network attacks, which could be designed to damage, destroy, or disrupt computers and networks. - Terrorists — Terrorists seek to destroy, incapacitate, or exploit critical infrastructures in order to threaten national security, inflict mass casualties, weaken the economy, and damage public morale and confidence.
- Insiders — Within the aviation industry, these insiders include personnel employed by airports, airlines, and other aviation stakeholders, including vendors, suppliers, and subcontractors, that may have access to airplanes or secure areas in airports or in sensitive locations off the airport site.
Spoofing is one such area of flight operation disruption in which bad actors could compromise an airplane’s navigational system in ways that “could make the airplane seem to disappear from the skies” or even create “the appearance of nearby ‘ghost’ airplanes, which could cause a pilot to alter an airplane’s course.”
“Someone with authorized access could intentionally or unintentionally misuse flight data, commercial components within avionics systems could contain vulnerabilities that enable cyberattacks, and malevolent hackers could seek to disrupt flight operations with various types of attacks on navigational data” — GAO report
The GAO report summarizes that “critical data used by cockpit systems could be altered, someone with authorized access could intentionally or unintentionally misuse flight data, commercial components within avionics systems could contain vulnerabilities that enable cyberattacks, and malevolent hackers could seek to disrupt flight operations with various types of attacks on navigational data.”
Other vulnerabilities lie in the integrity of supply chains themselves. According to report:
Without adequately assessing the security practices of manufacturers and thoroughly testing electronic components, cybersecurity vulnerabilities can be introduced to avionics systems at multiple points within insecure supply chains. This could potentially result in a range of impacts, from allowing an adversary to take control of a system to decreasing the availability of materials needed to develop a system.
Within commercial airplanes, software and hardware compromised by malware could enable malicious persons to perpetrate exploits after the compromised parts are installed on the airplane. Additionally, supply chain failures could create exploitable defects. Airplanes feature electronic hardware components known as line replaceable units, which could be compromised and adversely affect flight operations. It is also possible that counterfeit line replaceable units containing malware or other security vulnerabilities could be inadvertently installed.
The GAO concluded that while the FAA has taken steps to coordinate cybersecurity issues, the “FAA has not conducted an overall assessment of the cybersecurity risks to avionics systems, and it has not developed policies and procedures for overseeing the implementation of avionics cybersecurity controls based on such an assessment.”
“To date, there have been no reports of successful cyberattacks on an airplane’s avionics systems” — GAO report
In order to strengthen its avionics cybersecurity oversight program, the GAO recommended that the FAA complete the following six steps:
- Conduct a cybersecurity risk assessment of avionics systems cybersecurity within its oversight program to identify the relative priority of avionics cybersecurity risks compared to other safety concerns and develop a plan to address those risks.
- Identify staffing and training needs for agency inspectors specific to avionics cybersecurity, and develop and implement appropriate training to address identified needs.
- Develop and implement guidance for avionics cybersecurity testing of new airplane designs that includes independent testing.
- Review and consider revising its policies and procedures for monitoring the effectiveness of avionics cybersecurity controls in the deployed fleet to include developing procedures for safely conducting independent testing.
- Ensure that avionics cybersecurity issues are appropriately tracked and resolved when coordinating among internal stakeholders.
- Review and consider the extent to which oversight resources should be committed to avionics cybersecurity.
According to the GAO, “FAA concurred with five out of six GAO recommendations, but it did not concur with the recommendation to consider revising its policies and procedures for periodic independent testing.
“The GAO clarified this recommendation to emphasize that FAA safely conduct such testing as part of its ongoing monitoring of airplane safety.”
CBP doesn’t consistently notify air travelers about facial recognition tech use, privacy: GAO
How healthcare is vulnerable to cyber attacks, assassinations & geopolitical agendas