The majority of government sponsored COVID-19 tracing apps are improperly secured, and in their rush to market, app developers leave users vulnerable to invasions of privacy, according to a new report.
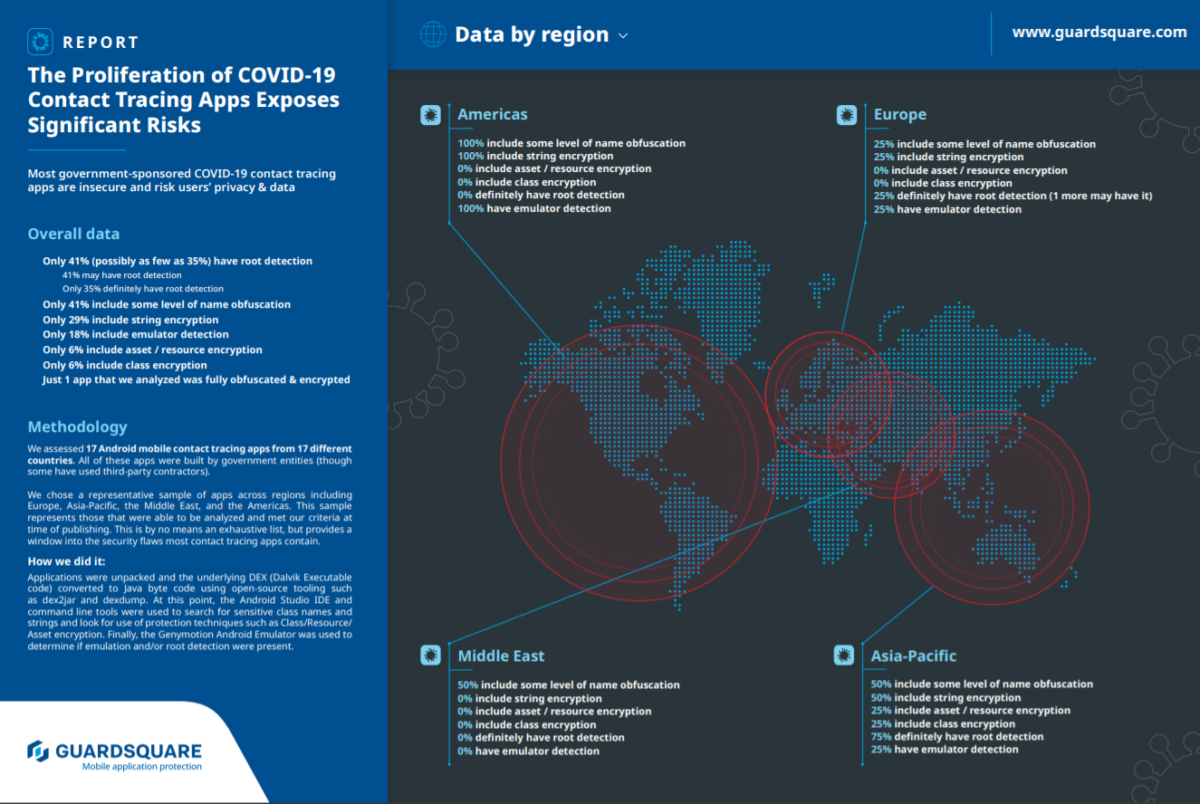
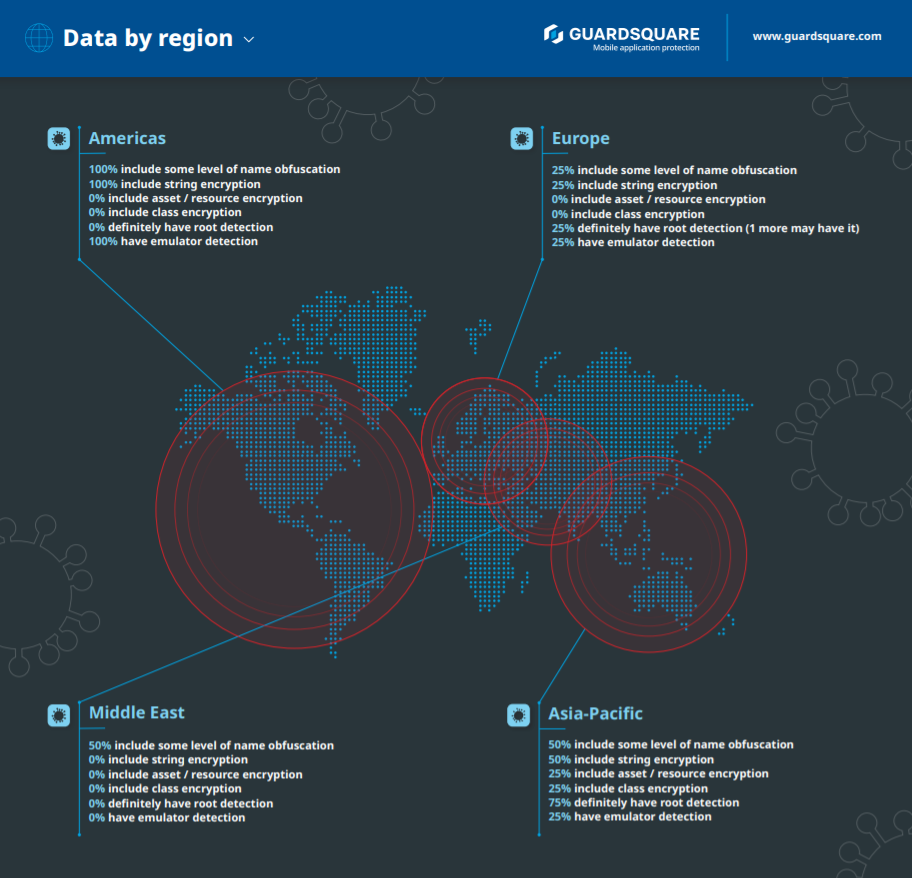
Today, mobile app security firm Guardsquare released a report called “The Proliferation of COVID-19 Contact Tracing Apps Exposes Significant Security Risks” in which it assessed 17 Android mobile contact tracing apps from 17 different countries across Europe, Asia-Pacific, the Middle East, and the Americas.
The report concluded that most government sponsored COVID-19 tracing apps leave widespread vulnerabilities where “malicious individuals may interfere with these apps for nefarious purposes, such as causing confusion, spreading false information, or instilling fear.”
“Hacktivists, especially in places experiencing civil unrest, may also disrupt these apps—not to steal or expose data—but because they dislike the idea of government or other surveillance,” according to the report.
Apart from being a privacy and security issue, unsecured contact tracing apps erode public trust in the apps themselves. This, according to Guardsquare, is a grave public health concern.
“Properly securing contact tracing apps is not just a citizen privacy and security issue and a government trust issue. It’s a public health concern as well,” according to the report.
If the whole point of contact tracing is to better understand how a virus is spreading, but people don’t trust it and therefore don’t use it, then contact tracing becomes useless in the attempt to stop the spread.
“Trust is key to success with contact tracing apps, but app makers unfortunately do not seem to be taking the risks seriously enough yet,” the report reads,” adding, “It only takes a single high-profile security incident to ruin confidence in an app.”
In order to make contact tracing apps more secure, Guardspace recommended that:
- All apps need to be developed securely and with a ‘privacy by design’ ethos.
- It’s up to governments and other entities who build these apps to ensure that the core code of the app is shielded properly, and that user information and privacy is safeguarded.
- Developers should use code hardening to protect code at rest and runtime application self-protection to protect apps in use.
- To be truly bulletproof, apps should implement hook detection, tamper detection, and debugger detection.
- Anyone disseminating contract tracing apps must impose minimum standards of quality and security on the third parties or internal teams who are developing them.
“Here is what governments and other organizations building COVID-19 contact tracing apps need to understand. If these apps are improperly secured (as most are), user data—in particular location information—may be at risk” — Guardsquare report
What data is being collected, who’s collecting it, how it’s being used, and how long it will be used for are all issues being debated across governments, think tanks, the media, and watch dogs when it comes to contact tracing technology and applications.
According to Guardsquare’s report, “These apps should not be gathering certain types of information, and certainly should not be storing it for any length of time. In particular they should not be monitoring absolute GPS location on an ongoing basis (it is more valuable and less invasive to monitor only geographic proximity to known infected individuals).”
Last month, the National Security Commission on AI published white paper by four of its commissioners stating that contact tracing apps can provide value in helping to control the spread of COVID-19, but that the apps should be “strictly voluntary” and without forced adoption.
Privacy advocates testify on preventing COVID-19 data from being exploited: Senate ‘Paper Hearing’